How to get a Finnish IP address
The easiest way to improve your digital privacy is to switch your IP address using a VPN. We’ll …

A new malware strain that can steal credentials and other sensitive information from victims without them knowing about it is currently making the rounds online. Dubbed the August Trojan, this malicious code can a steal a victim’s files and access their credentials, among others.
Proofpoint made the discovery in December 2016 after observing multiple, highly personalized campaigns from threat actor TA530, with customer service and managerial staff as major targets. During the analysis of these campaigns, Proofpoint found that the Trojan is contracted through files that are socially engineered to be downloaded by the victims. Below is one example of the emails:
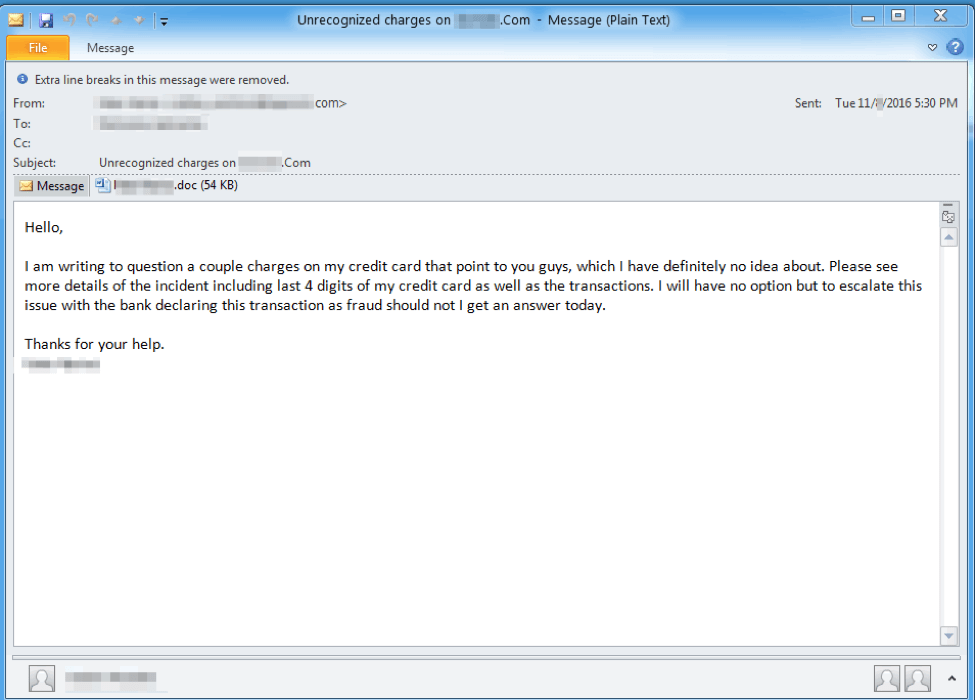
Upon infection, the August Trojan can steal:
While the August Trojan is currently being distributed via email campaigns, contracting it via other means like drive-by downloads and malvertising is possible.
Simple ways to stay secure against the August Trojan
Just like other malware strains, the August Trojan is highly dangerous, but only if you’re negligent. Preventing these malicious software programs from infecting your device is actually not impossible, and all it takes is a few simple steps.
One effective precaution is keeping your security software updated. Software updates contain a lot of patches that help cover current and potential vulnerabilities in your software – vulnerabilities which most of the malware strains today need to abuse in order to successfully infect devices.
Another must-do is making sure that your firewall is up at all times. While not enough to secure your device on its own, firewalls offer basic protection against network threats, including malware strains like the August Trojan, by preventing your device from getting in contact with untrusted networks.
Another effective security measure is practicing good judgment–when visiting websites, clicking on links on social media sites and in emails, and downloading files. Don’t click links on websites that are not well-known. If a website seems suspicious to you, leave the site immediately. Signs of websites being suspicious include having a lot of “Download” buttons, pop-up windows, page redirects, and blatant spelling mistakes.
Additionally, you can improve the security of your device against malware attacks by connecting to the Internet using a VPN. One notable example of this is Hotspot Shield, an anti-malware VPN that prevents malware infections by blocking websites and links that are known to carry malware. This provides added malware protection for your device without the need to pay, as Hotspot Shield can be downloaded for free.
Hotspot Shield, the best anti-malware VPN
If you’re looking for an anti-malware VPN to complement the protection offered by your firewall and security software, the best choice is Hotspot Shield VPN. Connecting to the Internet via Hotspot Shield VPN allows worry-free online sessions by notifying you if you’re visiting a malware-infected website. Hotspot Shield then blocks access to that site.
Downloading Hotspot Shield also lets you enjoy additional benefits, including:
Don’t let the August Trojan steal your sensitive information by downloading the best anti-malware VPN today! Hotspot Shield is compatible with most Windows, OS X, Android, and iOS devices. It is also available as an extension for Google Chrome and Mozilla Firefox. Visit the Hotspot Shield website and read our other blog posts to learn more.
