What is a Firewall?
A firewall is a software or hardware system designed to prevent unauthorized access to an individual computer or network of computers. They are used mostly as a first line of defense to protect your device or network from online threats such as hackers, viruses, Trojans, and worms.
Every time you are connected to the Internet, your computer is exposed to all sorts of dangerous programs and malicious people that want to infiltrate your computer to steal your personal information, send spam emails to your inboxes, or use your computer to launch attacks on other computers.
A good firewall system blocks attackers from trying to infiltrate your system and prevents your data and information from flowing out to the bad guys.
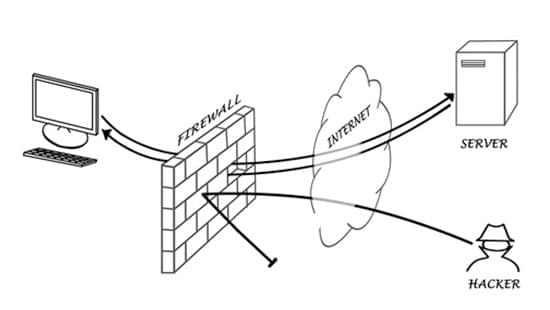 Figure 1. Like a brick wall, a firewall acts as a barrier to protect your computer from online threats
Figure 1. Like a brick wall, a firewall acts as a barrier to protect your computer from online threats
Firewalls have a similar function as the drawbridge and the portcullis grate in front of the entrance on a medieval castle – controlling who can go in and out.
While a castle has its fortified entrance through which both the defenders and attackers have to pass, a computer – either a standalone machine or computer network –has its firewall at the access point for connecting to the outside world.
Hardware vs. Software Firewalls
A firewall can be implemented using either software or a separate physical device (usually for large networks) or a combination of both.
Hardware firewalls are built into the routers. They are designed to protect all the devices connected to a network . If you are connecting to the internet through a broadband router, the router’s firewall is already protecting your device.
Software firewalls are included in Microsoft operating systems such as Windows XP, Vista, 7, 8, and 10 and it is turned on by default. Window’s firewalls generally provide less protective features than those purchased from antivirus vendors. One notable feature missing from Windows has been two-way controls to restrict what travels out from your device as well as what comes in.
Firewalls made by internet security companies can provide two-way protection and may also block malware and other malicious programs.
Firewalls Examine Data Packets Entering and Leaving the Network
Firewalls essentially work by examining data packets entering and leaving your computer or network.
In particular, a firewall looks at the sender/recipient IP addresses and the TCP/UDP port information to see if this agrees with the security rules defined by you or your network administrator. Packets that fail to match the given rules or criteria are either dropped or rejected. This prevents hackers from getting into your device and stealing your personal information such as your passwords and bank account numbers.
Filtering packets of data is at the core of how a firewall operates. Modern firewalls can filter traffic based on many packet attributes such as the IP addresses of the source or destination, domain names, key words, applications sending and receiving the data, and specific ports.
There have been many changes to the mechanics of how this is done since the theoretical concept of a firewall was publicized in 1988.
Analyzing a Packet’s “State of Mind”
Packet filtering only allows packets to pass through the firewall if they match the established rules. These rules can be either set by default or specifically defined by the computer’s administrator.
These filters look at each packet individually, usually by looking at the IP addresses of the sender and recipient and the port number. In addition, they don’t analyze whether or not a packet is part of larger stream of traffic or store information about the “state” of the specific connection. For this reason, they are called “stateless” filters. A stateless firewall requires less memory, and can be faster than the more advanced stateful” filters. However, they are unable to make decisions based on the overall communication between hosts.
“Stateful” firewall filters are able to distinguish between the various types of packets used for different types of connections. They do this by keeping packets long enough to decide on the overall “state” of the communication stream and determine whether or not a packet is the beginning of a new connection, part of an ongoing connection, or not part of any connection. A “stateful” firewall can have the connection state as a criteria in addition to the preceding static rules.
Application firewall filters look closer at the specific applications and protocols being used. This background helps the firewall determine if an unwanted message is trying to bypass the firewall by using a different port, manipulating the basic structure of a protocol, or encapsulating data within SSL encryption.
In practice, many firewalls use several techniques in concert.
A Firewall Doesn’t Provide Comprehensive Protection
One thing to note is that a firewall only acts as a first line of defense. It doesn’t provide comprehensive protection against all threats such as most viruses, spam messages, and malware.
If you want a more comprehensive protection for your device, you should also install the latest antivirus and antimalware programs.
Additionally, a VPN is recommended to secure your web browsing and your WiFi internet connection at public WiFi hotspots. A VPN encrypts all your internet traffic, which prevents hackers and snoopers from stealing your private information.
Additional Resources:

Download Hotspot Shield VPN. It’s Free!
Join over 650 million users already enjoying absolute Internet Freedom around the world by downloading Hotspot Shield VPN.